Simple fixes for safe surfing (of the cyber kind)
For all its benefits, the internet and electronic communications are fraud with peril. Read about several simple fixes for safe surfing of the cyber security kind.

7 Tips for spotting scams and phishing expeditions
Let's face it, the internet and electronic communications, i.e., email, messaging and text, grow more perilous by the day. The bad guys out there are persistent and inventive, developing new viruses and malware to steal identities, financial information and any other data they can sell for fun and profit.
When I receive an obvious phishing email, my primal tech fantasy kicks in, "Man, I wish I had the mad skills to turn it right around and blast the bad guys with a dose of their own medicine." Alas, I do not possess such skills. Instead, I have a suspicious nature and a fair amount of experience in fortifying my computers and information against nefarious attacks. So, let's dive into the steps that'll keep you safe(r) on the down and dirty internet.

If volume equals quality, then I have one of the best inboxes!
The sheer volume of emails hitting my Inbox, legit and not, is several hundred every day. Yes, that's largely my fault for subscribing to so many interesting sites. My email client is Outlook.com, the free online version of the desktop Outlook app, the freaking best email client ever.
But I digress. Outlook.com flags potential spam and phishing emails, tossing them into the Junk folder. Here's a screenshot of some of the 160+ emails from this morning.
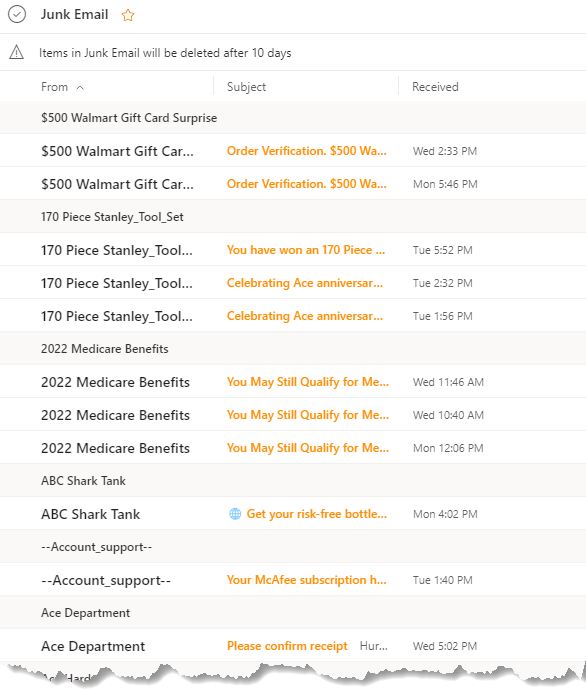
I like to go through them a couple of times a day, blocking most, reporting phishing and moving legitimate emails to my Inbox. Some folks simply empty the Junk folder. That would be a mistake for me because important emails often end up in the junk pile.
7 Tell-tale signs of spam and phishing attempts
Fortunately, most phishing and spam emails send out signals for you not to open or click. Here are the seven signs I look for to classify an email as legit or bogus. To guide your study of what to look for, I offer you the following email anatomy chart. Hey, it's even conveniently numbered to correspond to the descriptions below the image! No need to thank me, it's "what I do*."
*I heard a 12-year-old kid on my grandson's baseball team say that after they shut down the other team in one inning.
Now for the anatomy chart.
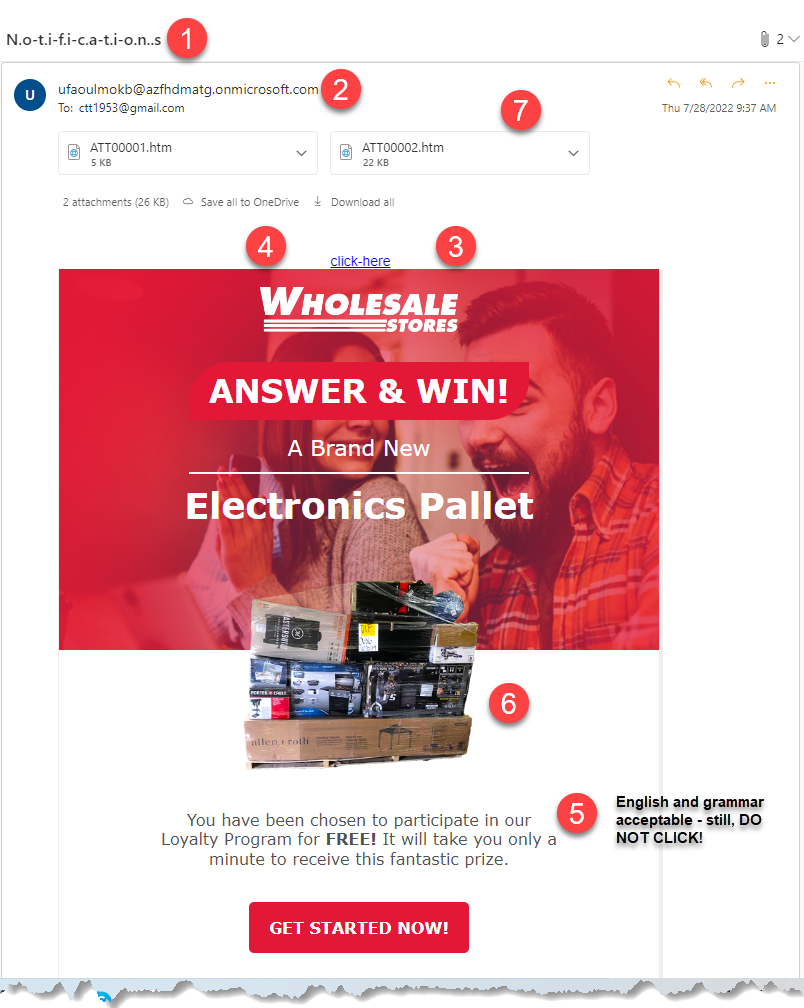
Right, let's talk about each point.
1. Unprofessional subject line format
Why do spammers and phishers use such odd subject lines? Simple, they do this to spoof browser algorithms that look for spammy and phishy wording.
Every now and then, I'll see a legitimate company do something similar, but that usually involves inserting a period rather than a space between each word. For example: Eat.At. Joe's. Don't get me started on what I think of the practice...
2. Bizarre and unrealistic email addresses
Maybe these emails will fly on Bizarro World, but c'mon, dude, no one has an email address like that. Why, then, use such obviously fake addresses? My thoughts are the practice helps evade blacklists of known bad actor email addresses. More on white and blacklists later.
3. For products and services you do not use
Ask yourself if you've ever done business with the purported sender of the email. In this example, I've never even heard of the company, Wholesale Stores. Red flag!!
However, the bad guys send emails featuring companies or products you do use. The following stores appear in my Junk folder regularly that I patronize:
- CVS
- ACE Hardware
- Lowes
- Home Depot
- Walmart
The list goes on and on. On the bright side, even these "brand name" emails use the techniques in this list, making them easy to spot.
4. Incorrect corporate logo use or made-up logos
All major corporations have strict branding guidelines and logo cops who enforce their use. Take a look at the logo. Is it distorted? Are the colors off? Those are a few spam indicators but be careful; the folks creating these digital gifts are getting good at mimicking proper logo use.
I found the Wholesale Stores logo in the anatomy chart vaguely familiar. However, I knew it was bogus, not having a wholesale chain account. For the sake of this article, I researched the name and came up with bupkis.
So, if the logo and layout don't look right, or you don't recognize the company, ditch the email -- safely. More on this later, too.
5. Poor grammar and English
Trust me when I say most people creating these little gems are not native English speakers. When you see grammar and wording worse than high school grammar dropouts, flee! It's either not legitimate, or you don't want to do business with a company with such atrocious mastery of our native tongue.
Now, in the anatomy chart, the English and grammar are good, but you still shouldn't click the links because there are so many other red flags.
6. Too good to be true or telling you something dire will happen soon
"Wow! You mean if I click the link and fork over some personal information, I can win a Brand New Electronics Pallet, whatever the dickens that might be?" No, that is not what it means, or at least not what will happen.
This definitely falls into the "too good to be true" bucket, along with perhaps the most famous phishing letter from the Nigerian Prince who's stolen a few million dollars and needs someone he can trust to hide it in their bank account. Let's break this famous phishing email down:
A. Nigerian Prince, obviously a crook, seeks a trustworthy person to hold his ill-gotten gains. You ask, "How trustworthy is a crooked Prince?"
B. Out of the billions of people using the internet, he has miraculously selected you for the scheme. You ask, "What's the probability of that?"
C. Look at it like a personal post, "Crook seeking trustworthy rube to hide money, all I need is your banking information." Would you want to meet up with that person? Me either, dump the email.
Note: These kinds of emails can be entertaining to read. I recommend doing it in preview panes.
A popular scam these days warns that your antivirus subscription, either McAfee or Norton, has expired, and you must click here to renew coverage ASAP. Now, if you have one of those products (I have Norton), do you click that link? Hell, no! Go directly to the actual website and check your subscription status.
Another favorite attack comes disguised as a well-known financial institution with which you may or may not do business. These phishing emails are among the best in recreating the actual bank's look, layout and language. They typically tell you something like your account has been compromised, and you need to click the handy link to change your password. You might call these physic emails because they predict what'll happen if you click through; you'll compromise it for them. Go directly to the website and log in there.
Warning, Will Robinson: Phishing and spam attacks are now showing up in text messages.
7. Attachments
Legitimate emails rarely come bearing attachments (a variation of the old pun, "Beware of Greeks bearing Trojans") unless you have requested a paper or something. An attachment makes the perfect place to hide a virus, piece of malware or other exploits. Images are another place nefarious phishers and spammers hide their evil "payload."
8. You weren't expecting anything from the sender- bonus flag
Expecting anything from the company or person? Be cautious and run the seven checks before clicking on anything.
Does an email need all seven indicators to classify as spam or phishing?
Nope, just one can be enough to make the correct determination. And, even if it was legitimate, they'll contact you again.
6 Protective measures you can take
Now that you understand the anatomy of spam and phishing emails let's look at the steps you can take to protect yourself.
1. Get a good antivirus and firewall app
When it comes to defending yourself, firewalls and antivirus apps need to be your first line of defense. The best of these apps stop dangerous attacks before they reach your PC.
Note: Good apps aren't cheap but are worth the expense if it protects your identity, financial well-being, the data on your drives and the PC hardware itself.
So, which app or combination of apps do you choose? My money is on Norton. I've used them for many moons and am pleased with the protection provided. Depending on how you configure the app, it can prevent you from opening malicious sites, scan and quarantine infected files and much more. And it has a VPN, which we'll cover later.
Or, you can take advantage of Windows' built-in security features. While not as robust as 3rd party apps, they provide reasonable protection and are free.
Finally, you can roll your own package combining excellent freeware apps. This used to be my approach, and it worked nicely. However, the apps required manual updates to keep their virus definitions current, something easy to overlook. When I rolled my own, I used these apps:
Avast AntiVirus - still protects millions and is well regarded by the tech world.
ZoneAlarm Firewall - one of the earliest "prosumer" apps the regular PC user could configure and manage.
2. Use proper passwords
Don't be that person who uses an obvious password for every account. It's rather remarkable, at least to me, that people still use horrible passwords like 123456, password, qwerty and 11111111. Check out the list of the worst passwords for 2022 at Tom's Hardware. If you use any of those, change them immediately!
Adopt and use a password manager
Digital security professionals recommend creating "strong" passwords and using a unique one for every account. Oh, and change them every few weeks. Sure, that's a piece of cake for someone like me with hundreds of sets of login credentials. As a compromise, I use arcane passwords for each site, storing them in my password manager.
But before we get into password managers, what is a strong password? It looks something like this:
bjiFz-MB$3#nWn_rLp as opposed to 123456
By definition, strong passwords have 8-15 characters and use upper and lowercase letters, numbers and special characters (the stuff above the number keys). Most sites clearly state their password requirements and let you know what it thinks of your password strength and if it meets the password rules.
For a long time, I kept an Excel spreadsheet with my login credentials. The problem with this and paper records crops up when entering them to access your account. You can copy and paste from a spreadsheet, but not from paper records.
In an issue of my PC magazine, I saw a review of the password manager, RoboForm. Feeling the app fit my needs, I subscribed, and over 20 years later, I am still happily using it.
Like antivirus and firewall apps, there is a myriad of password managers, free and paid. Read some reviews and try a couple out via free trials. Make sure RoboForm makes the list. Pick the one that strikes your fancy.
Many browsers offer to save your passwords. While I do this to some extent, I am nervous about storing passwords in software that bad actors hack into for data.
3. Blacklisting and whitelisting emails
Blacklists contain email addresses you never want to see in the Junk folder or email again. You create your lists inside your email application. To blacklist an email sender, select an email and click either the Block or Phishing buttons.
Whitelists contain the email addresses you've deemed safe and want to receive. When you find an email in the Junk Folder that isn't junk, click the Not Junk button to move it to your Inbox. You can see the buttons from Outlook.com below:

Note: I have a gripe with Outlook.com and its habit of ignoring my Whitelist designation. It may take many attempts to convince Outlook that an email is okay. Here's what I do whenever Outlook miscategorizes an email:
- Click Not junk.
- Right-click on the email inside my Inbox and click Add to Safe Senders.
- Repeat until it sticks, or you unsubscribe in frustration.
Don't click Unsubscribe in a spam or phishing email
Normal humans figure they can solve the problem by unsubscribing from the noxious communication. DO NOT click that link. Why, you ask? First, it's a link in a tainted email and may launch the nasty goody hiding inside. Second, you've identified your email as valid and operating even if it is a real unsubscribe button. These fine folks sell that information to their buddies, sharing the wealth, so to speak, opening you to even more spam. Block it or report the email as phishing instead.
4. Address book preemption
We all know someone who has had their address book hacked or experienced it firsthand. The practice seems less common now than 20 years ago, but it continues today. The objective of this exploit is to gain access to another list of emails they can send malware.
A long time ago, in a century bygone, someone gave me a simple trick to protect my address book. They had me create a fictitious email address that always sits in the number 1 spot. Here's an example:
__abcdef (not having the @ and domain is done on purpose)
It works this way; the bad guy's software collects addresses until it hits a bad email address, and then it stops looking. The two underscores followed by the letter "a" ensure the bogus email remains in the pole position, preventing the theft before it starts.
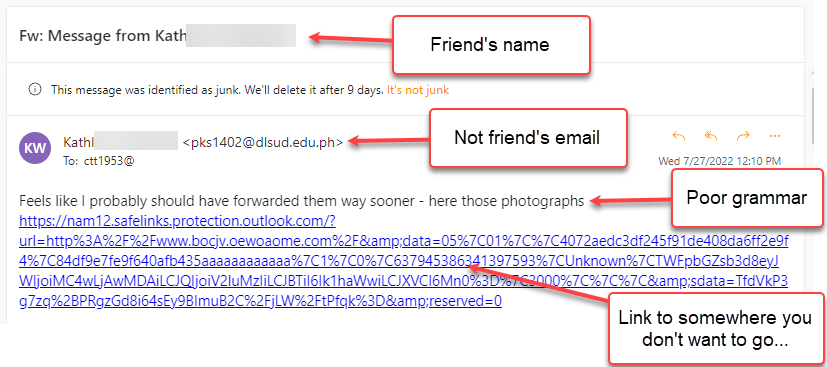
Here's an example of a friend who suffered address book piracy.
I know it isn't from the friend for the reasons in the comment boxes, plus I was not expecting to hear from them. This last bit isn't too much of an indicator, just another piece of evidence:>) I told the person how to fix it. Unfortunately, they cannot implement it and live on the East Coast out of reach.
5. Use a VPN
Virtual Private Networks (VPN) used to be the provenance of super IT geeks, being exceptionally complicated to create. Today, the VPN has become ubiquitous, especially on mobile devices. How does a VPN work, and what does it do for your internet security?
A VPN program creates a secure, encrypted connection between your computer or device and a predetermined destination, say a corporate network. Most corporates use this connection when employees access corporate networks from the outside world.
Aside from encrypting your data, a VPN also hides your computer's IP address. For general web access, the VPN app connects your computer to a server in another location. It then shows a new IP address to any sites you visit. You may end up surfing from another city or country.
The VPN downside
VPNs do a great job protecting you and your data, but that comes at a cost, reduced connection speeds. The VPN process requires a lot of processing power and can significantly reduce connection speeds. For casual surfing and shopping, it's not much of an issue. But, for gaming or working with large files, it borders on being unacceptable.
For example, during COVID, I worked for a client editing large documents. Connected via the corporate VPN, opening, saving and closing documents took as long as 30 minutes! Let's say it was a productivity killer. Significantly reduced frame rates are the problem when playing online games. It spoils the fun and can cause you to lose your championship status in whatever game you're playing.
Does this mean you shouldn't get and use a VPN? Not at all. They are potent tools, but you have to use them judiciously. I turn it off for gaming and transferring large files. I turn it on when using my phone outside my home network. Like all technology, VPNs are constantly improving. When shopping for one, look for those you can adjust to meet your current task.
6. Back everything up to the cloud or a dedicated drive outside your PC
Ransomware, viruses and other malware can lock up, delete or destroy your files. Seeing as how that's the case, you need a solid backup plan that saves your files on the cloud or a hard drive outside your PC. Backup drives in the PC won't help if a virus or other nasty gets loose.
There are tons of choices. Since I subscribe to Microsoft 360, my files reside in my OneDrive account. I also have files backed up to iCloud, although that option leaves much to be desired in my experience.
Does having a backup work? Absolutely. While attempting to upgrade my PC's power supply, I fried the computer and both drives. Once I logged into my Microsoft account from the new machine, OneDrive restored files, folders and recent documents all by its lonesome. It didn't get it all, but it got most of what I needed. While the problem wasn't the result of a virus or some malware, it was an excellent simulation.
Now get out there and shore up your defenses
The internet is a marvelous place, the modern-day Library of Alexandria, as I like to say. It bestows remarkable powers for shopping and learning on the ordinary person and making what I do for a living possible.
The internet also has a wild side, with plenty of pitfalls for the unwary and unprepared. Remove yourself from both categories, stay alert, and invest in your digital defenses. Remember, electronic abstinence is the only 100% fool-proof way to prevent contracting an internet-transmitted disease; unplug your computer and devices from the net. Now, where's the fun in that?
